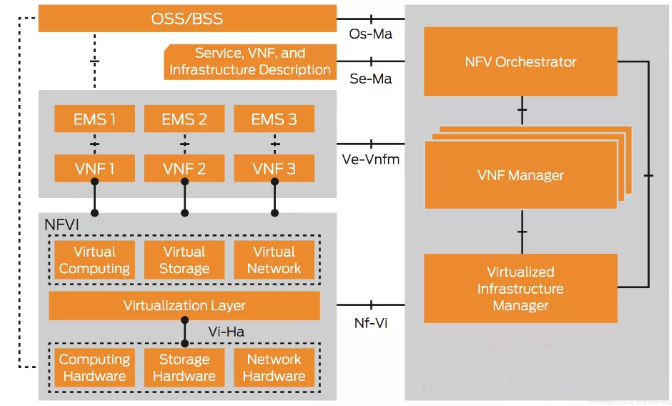
Today, I will tell you about terminal access technology. Terminal access means that the terminal device is connected to the router, and the data communication between the terminal device and other terminal devices is completed through the router.
The terminal access implemented by the router is divided into two types: the terminal access initiator and the terminal access receiver.
The terminal access initiator is the party that initiates the TCP connection request, as the client of the TCP connection, generally a router;
The terminal access receiver is the one responding to the TCP connection request. As the server of the TCP connection, it can be a front-end processor or a router.
Whether the router is the initiator or the receiver, as long as the TCP connection is established, the data stream on the terminal device can be transparently transmitted to the opposite end of the TCP connection.
Generally speaking, there are five types of terminal access:
1
TTY terminal access: the initiator is the router, and the receiver is the front-end processor. The service terminal is connected to the router through the asynchronous serial port, and the router is connected to the front-end processor through the network. The application service runs on the front-end processor. The front-end processor interacts with the router through the ttyd program, and pushes the business screen to the service terminal through the router. The router is responsible for the transparent transmission of data between the connected service terminal and the front end processor.
2
Telnet terminal access: The service terminal is connected to the router (Telnet Client) through the asynchronous serial port, and the router is connected to the front-end processor (Telnet Server) through the network. The application service runs on the front-end processor. The front-end computer interacts with the router through standard Telnet. Then establish a data channel between the terminal and the front end processor.
3
ETelnet terminal access: The service terminal is connected to the router (ETelnet Client) through the asynchronous serial port, and the router is connected to the front-end processor (ETelnet Server) through the network. The application service runs on the front-end processor, and the front-end processor communicates with the router through a specific encrypted Telnet. Interaction, and establish a data channel between the terminal and the front end processor.
4
SSH terminal access: The business terminal is connected to the router (secure shell) through the asynchronous serial port, the router is connected to the front-end computer (SSHServer) through the network, and the application service runs on the front-end computer. The front-end computer interacts with the router through standard SSH, and then Establish a data channel between the terminal and the front-end processor.
5
RTC terminal access: The RTC initiator is a router, and the receiver is also a router. RTC terminal access is another typical application of terminal access. It establishes a connection between a local terminal device and a remote terminal device through a router, completes data interaction, and realizes data monitoring functions.
In asynchronous RTC mode (RTC currently only supports asynchronous mode), the monitoring terminal in the data center and the remote monitored terminal are connected to the router through an asynchronous serial port, and the routers exchange data through the IP network.
Generally speaking, the router connected to the monitoring device acts as the initiator (RTC Client), and the monitoring device can initiate a connection at any time to obtain the data of the monitored device. The router connected to the monitored device acts as the receiver (RTC Server), which can receive the connection request of the monitored device at any time to send the monitored data.
The above is the news sharing from the PASSHOT. I hope it can be inspired you. If you think today’ s content is not too bad, you are welcome to share it with other friends. There are more latest Linux dumps, CCNA 200-301 dumps, CCNP Written dumps and CCIE Written dumps waiting for you.